Phishing attacks are constantly evolving and becoming more sophisticated, if you don’t know what to look for, it’s very easy to become a victim. Whether it’s a fake password reset, or what appears to be a genuine email from someone you know – it’s the tiny details which give these attacks away.
“91% of cyberattacks and the resulting data breach begin with a spear phishing email” – https://cofense.com/enterprise-phishing-susceptibility-report/
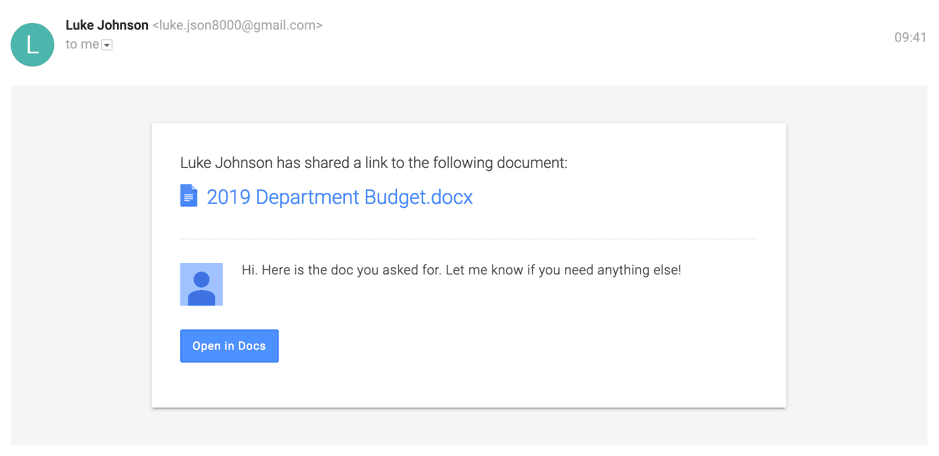
What if Luke Johnson was someone you knew well, would you open this?
Visually, this phishing email is the same as what you would usually receive when someone shares a document with you. Early on a Monday morning, half asleep, it would be very easy to open this, input your login details, and compromise yourself and your company. So how can you protect yourself from this type of attack?
Fake Links
When someone sends you an email like the below, where the link is not directly visible and you are encouraged to click the ambiguous button to get to the content, you should always check where the button leads to before clicking.
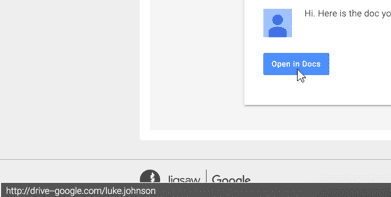
By hovering the mouse cursor over the button and not clicking, you can see where it leads to at the bottom-left of the screen.
This link leads to “http://drive–google.com/luke.johnson”. Google Drive is usually “https://drive.google.com”, and this link does not follow the signature of a shared file, it just has the name of the sender at the end of it and not unique identifier for a file. It’s very safe to then assume this is a phishing attack, and it would be a good idea to report this to the administrator and inform your coworkers.
Prerequisite knowledge: Subdomains. To put it simply, a subdomain is a part of a larger primary website. For example, “https://docs.google.com”, “https://drive.google.com”, “https://mail.google.com” – ‘docs’, ‘drive’, and ‘mail’ are all subdomains (parts) of google.com.
Another example of lookalike URLs would be: “http://drive.google.com-personal.net/file/fe9FjvneD9aLe”
The URL begins with ‘drive.google.com’, so at first glance it seems legitimate, but look closer and you can see that the website does not actually lead to google.com, but instead to the attackers website “com-personal.net”. “drive.google” is simply a subdomain of “com-personal.net”.
Spoofed links
An example of a spoofed link would be as such: https://google.com. This link appears to go to Google, however when you mouse over it – you can see it actually goes to “https://bing.com”. This attack vector could incite you to click a seemingly normal link, but it’s actually a link to the attackers site.
Redirection
Another similar and easy to miss method is using Google’s redirection service to send a clicker to a hackers site.
https://www.google.com/amp/x9f8ehajdkfuvme.com
The ‘amp’ part of this URL will send the clicker to the website at the end of the URL. So, someone might send you a link telling you it’s a link to a file on Google Drive, but it’s actually a trap sending you to the hackers site.
Fake email address
This kind of thinking doesn’t only apply to links – it applies to email addresses.
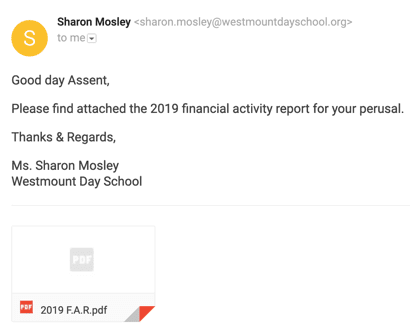
Usually, emails come from “westmountschool.org”. Attached is a PDF and at first glance everything appears legitimate. However, the giveaway is that the email is actually from “westmountdayschool.org” – the attacker has registered a domain to send emails from specifically for this attack, and the attached PDF likely contains malware.
Further reading
Using what you have learned here, click here to try Google’s phishing test. If you would like to learn more, why not try our phishing course over at Lorators?


